In network space, defending against network attacks and protecting information security is important, and intrusion detection is useful to determine whether a network packet contains an attack.
Preprocessing is the basis for better intrusion detection performance. Existing intrusion detection preprocessing methods usually require a large number of manual experience extraction features. Manually extracted features do not have the ability to accurately characterize network packets.
Signature-based detection is capable of detecting known attack behavior, and anomaly-based detection is used to discover unknown attack behavior by detecting the features of network packets. It is critical to find a feature set that characterizes network packets as accurately as possible. However, existing feature extraction methods suffer from low accuracy and low detection rate.
Researchers from the Institute of Acoustics of the Chinese Academy of Sciences (IACAS) investigated variant gated recurrent units (GRU) with encoders to preprocess packets for payload-aware intrusion detection, and achieved higher accuracy and detection rates than three of the state-of-the-art methods.
The study has been published online in the academic journal IEEE Access in April 2019.
There were two problems with the existing Intrusion Detection System (IDS) algorithm. One was that much manual experience was required to preprocess data packets for network packets. The other was the complex structure of neural networks leading to the disadvantages of large memory usage and increased power consumption.
For the first problem, researchers introduced the encoded gated recurrent unit (E-GRU). This algorithm used an encoder to automatically preprocess network packets. The encoder gave a better representation of the input than the original raw input, and the encoder was the compression of the input data which was the important features of the input. After that, the extracted features were used as the input to the GRU for intrusion detection.
For the second problem, researchers introduced the encoded binarized gated recurrent unit (E-BinGRU). Binary weights and activation of gated recurrent units with encoders were investigated for payload-aware intrusion detection to reduce memory size for the first time.
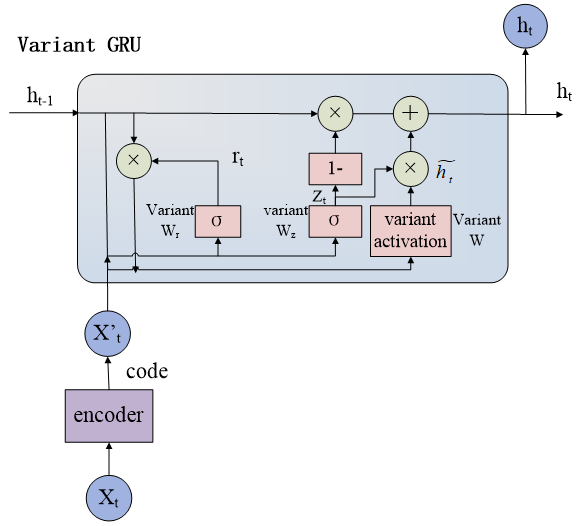
Figure 1. Structure of the proposed algorithm (Image by IACAS)
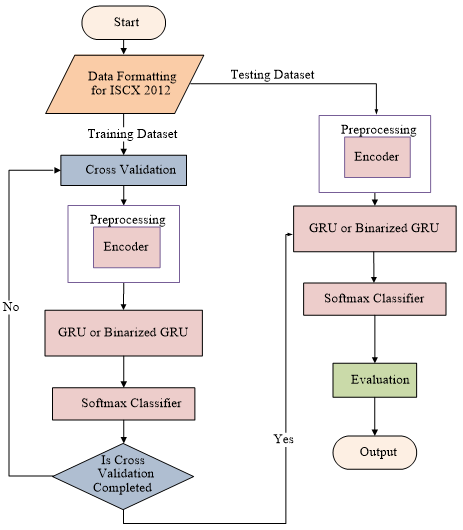
Figure 2. Flow chart of the proposed algorithm (Image by IACAS)
The proposed model was evaluated based on the ISCX2012 data set. Evaluation showed that the detection rate (DR) of the E-GRU reached 99.9%. E-GRU achieved the best performances regarding the DR of attack network packet exceeding those of the other state-of-the-art methods by 3%. The accuracy of the E-BinGRU was 99.7%, which was higher than that of the Bin-GRU without the encoder. The accuracy of the E-GRU was 99.9%, which was as high as that of the GRU.
The worst cases test confirmed the performance stability with respect to accuracy, detection rate, and false alarm rate. In order to reduce memory size, researchers used E-BinGRU for network intrusion detection. E-BinGRU drastically reduced memory size and replaced most arithmetic operations with bit-wise operations, which was expected to substantially improve power-efficiency. The results showed that memory usage shrunk to 1/21 by using binary weights and activation.
Reference:
HAO Yiran, SHENG Yiqiang, WANG Jinlin. Variant Gated Recurrent Units With Encoders to Preprocess Packets for Payload-Aware Intrusion Detection. IEEE Access, 2019, 7: 49985-49998. DOI: 10.1109/ACCESS.2019.2910860.
Contact:
ZHOU Wenjia
Institute of Acoustics, Chinese Academy of Sciences, 100190 Beijing, China
E-mail: media@mail.ioa.ac.cn


